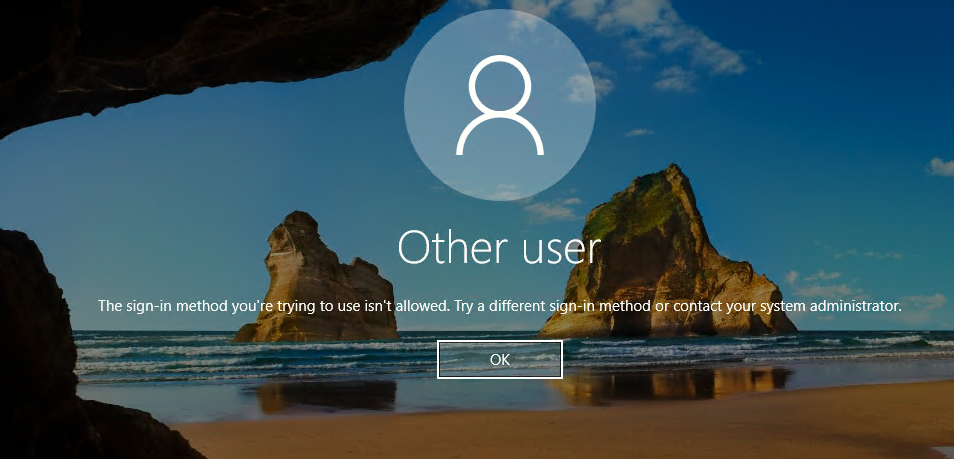
You can use Entra ID to login to Azure VMs without having to setup Entra Domain Services or AD join the VM, however you may encounter the error “The Sign-in method you’re trying to use isn’t allowed. Try a different sign-in method or contact your system administrator.” This is likely because the Entra ID you are trying to use is required to pass Multifactor Authentication (MFA) but Entra MFA is not supported at the Windows Login.
Understanding the issue
When an Entra ID-joined Azure VM is configured for user sign-in, it requires authentication through an Entra ID Enterprise Application called Azure Windows VM Sign-in (previously known as Microsoft Azure Windows Virtual Machine Sign-in). If a Conditional Access policy enforcing MFA applies to this sign-in flow, users attempting to log into their VMs with Remote Desktop Protocol (RDP) using their Entra ID may experience authentication failures.
Microsoft outlines this requirement in their official documentation:
Microsoft Documentation – MFA Sign-in Method Required for Azure AD-Joined VMs
The Fix: Excluding the Right Service Principal
To resolve this, you must exclude the following application from your Conditional Access policies enforcing MFA:
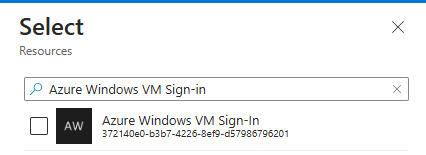
Azure Windows VM Sign-in
(Previously named Microsoft Azure Windows Virtual Machine Sign-in)
Important: The exclusion name must be precise—you cannot find it by searching for “virtual machine,” “VM,” or “sign-in” in the Conditional Access policy UI.
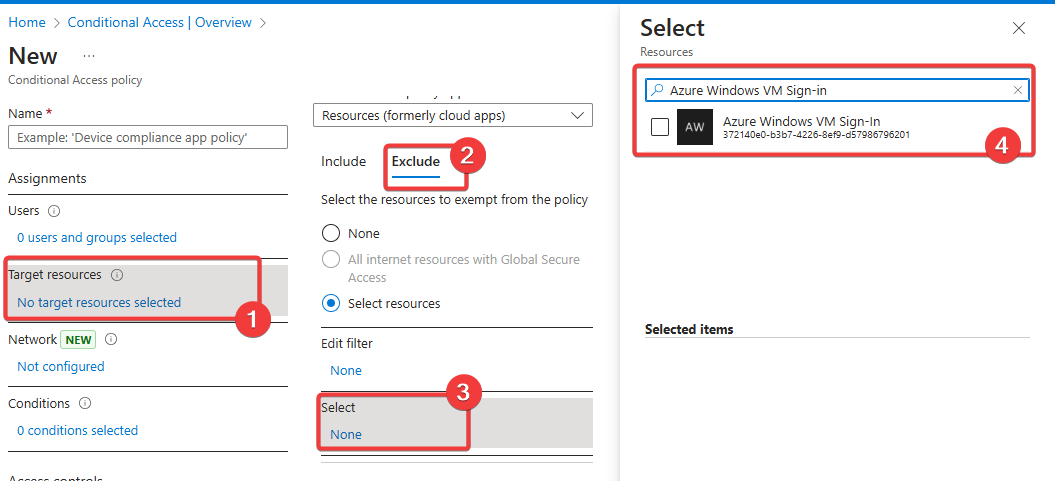
How to Exclude ‘Azure Windows VM Sign-in’ from MFA
- Sign into the Microsoft Entra admin center (https://entra.microsoft.com)
- Navigate to Protection > Conditional Access
- Select the Conditional Access policy that enforces MFA for sign-ins
- Under Cloud apps or actions, locate Include > All cloud apps
- Click Exclude
- Search for and select:
- Azure Windows VM Sign-in (or Microsoft Azure Windows Virtual Machine Sign-in, depending on your tenant’s naming convention)
- Save and apply the changes
Why This Works
By excluding Azure Windows VM Sign-in from MFA enforcement, you allow primary authentication to succeed while still enforcing strong authentication on other resources. So you maintain MFA requirement to everything else but allow the Entra ID VM sign in process through windows login to successfully authenticate without having to do unsupported MFA. This ensures security without breaking user access.
Final Thoughts
MFA is essential for protecting cloud environments, but misconfigured policies can cause unintended disruptions—like blocking Azure VM sign-ins. Precision in exclusions is key. By properly configuring Conditional Access exclusions, you ensure both security and usability for Entra ID-joined Azure VMs.

